Third-Party Risk Scoring & Tiering: A Comprehensive Guide

When businesses work with external partners or suppliers, they must ensure these third parties do not introduce risks that could harm the company. Third-party risk management (TPRM) addresses this concern. A key component of TPRM is third-party risk scoring, closely followed by vendor risk tiering.
Understanding these concepts is essential for building a robust third-party risk management foundation. In this post, we define risk scoring and tiering, explain how they fit into your overall TPRM program, and recommend best practices for implementation.
What Is Third-Party Risk Scoring?
Third-party risk scoring is the process of evaluating and assigning a numerical value to the potential risks that an external partner or supplier might bring to a business. This score helps determine how risky it is to work with that third party based on factors like their security practices, financial stability, and compliance history.
Risk scoring involves:
- Identifying Risks: Determine potential risks such as data breaches, financial instability, and regulatory compliance issues.
- Assessing Risks: Gather information on each third party, including financial health, security practices, and compliance history.
- Scoring Risks: Assign a score based on the level of risk each third party represents. For example, a company with strong security practices gets a low-risk score, while one with frequent security breaches gets a high-risk score.
What Is Third-Party Risk Tiering?
Third-party risk tiering is the process of categorizing external partners or suppliers into different levels or tiers based on their risk scores. These tiers help businesses prioritize and manage their third-party relationships according to the level of risk each partner presents.
Tiering involves:
- Creating Tiers: Decide on different tiers, such as high, medium, and low risk.
- Assigning Third Parties to Tiers: Place each third party in the appropriate tier based on their risk scores.
- Managing According to Tiers: Manage third-party relationships based on their tier. High-risk partners require more frequent reviews and stricter oversight, while low-risk partners need less intensive monitoring.
Why Is Scoring Risks and Tiering Vendors Important?
Different third parties pose varying levels of risk. The criteria for each tier will vary depending on the nature of the vendor. For instance, a parts vendor has different criteria than a cloud hosting service. Calculating and categorizing risk is important for:
- Protection: Helps protect your company from potential breaches and privacy violations traced to risky third parties.
- Efficiency: Allows you to focus resources on monitoring and managing the riskiest partners.
- Compliance: Ensures you meet regulatory requirements by systematically managing third-party risks.
By understanding and implementing third-party risk scoring and tiering, businesses can better manage their external relationships, minimize risks, and enhance overall operational stability.
Download the Free Profiling and Tiering Template
Apply consistent methodology to third-party profiling and tiering with this customizable document.

Utilize Scoring to Normalize Results and Provide Actionable Insights
Understanding the potential impact of a supplier's failure to deliver products or services is crucial. Leverage a scoring system to determine each supplier's tier based on criteria such as:
- Operational or client-facing processes
- Interaction with protected data
- Financial status and implications
- Legal and regulatory obligations
- Reputation
- Geography (e.g., concentration risk)
Once you define supplier tiers, identifying the most critical suppliers becomes straightforward. For example, you can run a report on all U.S.-based, top-tier suppliers that handle personal data.
Having vetted information early in the process and in an easily accessible location allows you to “right-size” due diligence initiatives, focus on the highest-risk vendors, and speed up the overall process.
How Do You Score Vendor Risks?
The basic calculation for scoring vendor risk is Likelihood x Impact = Risk. For instance, consider a vendor providing critical IT services to a financial institution but not complying with industry cybersecurity standards. The impact could be significant financial loss and reputational damage due to a potential data breach (e.g., major or severe impact), and the likelihood is the probability of a cyber-attack being successful due to the vendor’s non-compliance (e.g., likely or extremely likely). This scenario represents an unacceptable risk for any financial institution and would likely result in contract termination.
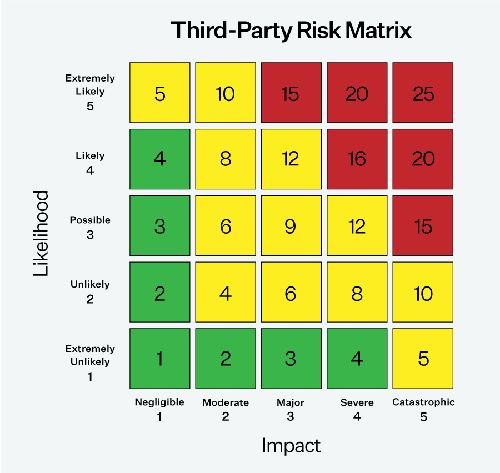
Utilize a matrix that combines likelihood and impact to determine the risk scores.
This example underscores the importance of conducting thorough vendor risk assessments with a comprehensive scoring rubric. This is especially crucial for organizations that handle sensitive information, such as financial institutions, government contractors, and healthcare providers. Often, regulations will hold the primary organization accountable for vendor non-compliance, emphasizing the need for diligent oversight and risk management.
Executive Brief: How to Get More from Third-Party Risk Scores
Discover how to build a more comprehensive, actionable and cost-effective vendor risk monitoring program.

Third-Party Risk Scoring Best Practices
Scoring risks and tiering vendors are essential to your overall vendor risk assessment. You should establish standardized controls and requirements. However, there is no one-size-fits-all vendor risk assessment process. Different vendors present varying levels of risk to your organization, depending on factors such as:
- Criticality to your supply chain, such as being a single-source or sole-source supplier
- Access to sensitive data, such as personally identifiable information (PII), protected health information (PHI), or commercially sensitive information (CSI)
- Susceptibility to continuity events, such as natural disasters or geopolitical conflicts
Having a structured process for each vendor category will make your third-party risk management program more efficient and help you make better risk-based decisions about your vendor relationships.
Define Your Acceptable Level of Residual Risk
In a perfect world, risk could be eliminated entirely. However, when working with any third party, some element of risk always remains. Before assessing potential vendors, define your acceptable level of risk. This step makes vendor selection and the entire third-party risk management process faster, more efficient, and uniform. It allows you to easily identify vendors that won’t meet your business objectives and risk tolerance and clarifies which controls you need to require of vendors.
Scoring Inherent Risk
Inherent risk scoring is a key part of the third-party risk management lifecycle. Not every vendor requires the same level of scrutiny. For example, an office supply vendor presents lower organizational risk than one providing critical parts or legal services. A vendor located in a politically volatile area with a history of breaches or a poor credit history poses more risk and requires increased due diligence.
To understand a vendor's risk, calculate inherent risk— the vendor’s risk level before applying any specific controls. This baseline guides your decisions on necessary due diligence. After establishing the inherent risk baseline, calculating the residual risk—the risk remaining after applying controls—becomes much simpler.
Inherent risk is also essential for vendor profiling, tiering, and categorization decisions. This approach speeds up risk assessments by aligning vendor evaluations with the risks and standards most relevant to your business, customers, and regulatory bodies.
Tiering and Categorization
Start with an internal profiling and tiering assessment to categorize your vendors and map out the type, scope, and frequency of assessments required for each group. A structured process for each vendor category makes your third-party risk management program more efficient and enables better risk-based decisions.
Leverage tiering based on inherent risk assessments to prioritize resources and efforts. High-risk vendors like billing or payroll providers may require more extensive assessments and monitoring. For residual risks, tailor mitigation strategies according to tiered categorization, focusing resources on high-risk vendors to ensure sustained compliance and risk reduction.
Leverage a Shared Library
Third-party risk management processes can strain under-resourced teams. Data collection and vendor communications account for most of the time needed to reduce risk and complete assessments. The ever-shifting regulatory landscape, requiring expertise to interpret compliance obligations, compounds this issue. Achieving compliance and meeting vendor risk management requirements while maximizing your team's skills is a balancing act.
To accommodate resource constraints, many organizations – especially those with a solid vendor tiering plan – choose to leverage completed content already submitted and shared within an industry exchange. These vendor exchanges are self-fulfilling prophecies – the more vendors participate, the greater the overlap with other enterprises. This speeds up the risk identification and mitigation process and minimizes data collection time.
Map Your Vendor Risk Assessment to Compliance Requirements
Ensure your vendor risk questionnaires reflect your organization’s compliance requirements. If your vendor has access to sensitive information such as PII, PHI, or financial data, map your compliance requirements to your vendor risk questionnaires. Key questions include:
- Is the organization certified to any third-party information security standards or frameworks? (e.g., SOC 2, NIST 800-53, NIST CSF, CMMC)
- Does the organization fall under cybersecurity or information security compliance requirements? If so, which ones?
- What policies and processes are in place for sharing customer data with third and fourth parties?
Don’t Go It Alone
Using a TPRM platform can dramatically speed up vendor risk assessments, aid in scoring and tiering vendors, and quickly map questionnaire responses to compliance requirements. Dedicated third-party risk management solutions like Prevalent offer built-in, customizable inherent risk questionnaires that make it easy to identify vendor risk seamlessly.
Discover how you can simplify and streamline third-party risk management with Prevalent. Schedule a strategy call or demo today.
-

How to Select a Vendor Risk Assessment Questionnaire
Discover the pros and cons of different vendor risk assessment questionnaires, and get tips for selecting...
07/09/2024
-

Vendor Risk Assessment: The Definitive Guide
Conducting a vendor risk assessment before onboarding a new supplier or giving a third-party access to...
06/24/2024
-

Comparing Third-Party Risk Management Approaches: A Deep Dive into Five...
The TPRM solution landscape can be complex, with hundreds of options available to address third-party risk...
06/18/2024
-
Ready for a demo?
- Schedule a free personalized solution demonstration to see if Prevalent is a fit for you.
- Request a Demo




